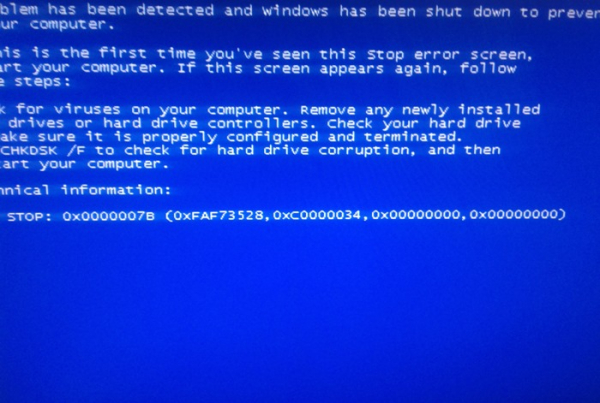
should read
The difference between Windows and Linux
 A small digression about Windows and Linux. Here you understand what’s the matter: Windows is a combination of the core of the system, as well as utility programs and scripts that perform certain operations and tasks. On this OS, you do not have the right to modify or delete scripts and system software …
A small digression about Windows and Linux. Here you understand what’s the matter: Windows is a combination of the core of the system, as well as utility programs and scripts that perform certain operations and tasks. On this OS, you do not have the right to modify or delete scripts and system software …
When you, for example, change the cursor on Windows, the cursor change job is executed by a script that is already in the system by default. A graphical interface has been written for the script (this is a separate program), which is also by default and which can neither be selected, nor changed, nor deleted. You press the button (graphical interface), run the script and the cursor changes. For Windows, there is one option for the cursor change program. All. You do not have the right to change this. Continue reading
Child lock
 I think many visitors to the site have children. Everyone certainly has a computer. And now you just have to turn away, as the child begins to play on the computer keyboard, like on a piano. As a result, anything can happen. Therefore, I am often asked questions about how to block a computer from small children.
I think many visitors to the site have children. Everyone certainly has a computer. And now you just have to turn away, as the child begins to play on the computer keyboard, like on a piano. As a result, anything can happen. Therefore, I am often asked questions about how to block a computer from small children.
Also, a lock is needed from time to time, when suddenly you suddenly realize that the keyboard needs to be cleaned, moreover, without delay. Locking the computer in this case is also a more convenient, practical and quick solution than turning off the PC during cleaning.
If you came to this page from a search engine for the computer is blocked, then you should read the article Continue reading