replacing capacitors
Linux operating systems
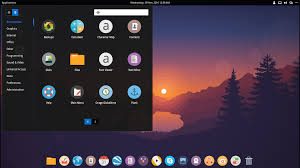 Linux is not an operating system, but just its kernel. Everything that you are accustomed to see and understand as an OS (buttons, windows and panels) – in fact, it is not. What you see is the GUI (Graphical user interface), that is, the graphical user interface, also called the graphical environment or graphical shell. GUI is a program designed to simplify the life of the user so that he does not suffer from the console. In fact, any OS looks like a console, that is, like the good old DOS.
Linux is not an operating system, but just its kernel. Everything that you are accustomed to see and understand as an OS (buttons, windows and panels) – in fact, it is not. What you see is the GUI (Graphical user interface), that is, the graphical user interface, also called the graphical environment or graphical shell. GUI is a program designed to simplify the life of the user so that he does not suffer from the console. In fact, any OS looks like a console, that is, like the good old DOS.
The types of operating systems built on the Linux kernel vary widely both in providing a working environment and in the set of applications available in the OS. This is partly because some programs Continue reading
Silent installation of applications (silent install)
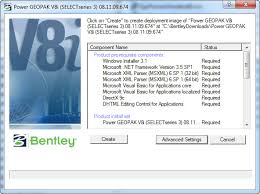 Silent installation is such a process in which you sit quietly and look at the screen where the software installation process takes place without your participation, provided that it is generally visible. At the same time, the installer does not bother you with questions like Do you agree with the license agreement ?. Installation options are used by default. those. those that the installer offers when installing the software in the usual way.
Silent installation is such a process in which you sit quietly and look at the screen where the software installation process takes place without your participation, provided that it is generally visible. At the same time, the installer does not bother you with questions like Do you agree with the license agreement ?. Installation options are used by default. those. those that the installer offers when installing the software in the usual way.
The disadvantages of a silent installation include all sorts of panels in browsers and E-Bay tags on the desktop, since most of these bonuses are included in the installation by default. But this is more likely an exception, although not rare. Read more about silent installation in this article. Continue reading
Bat files, examples
 You can execute all the examples published below not only by creating and running a BAT file containing these commands, but by copying them directly to the command line.
You can execute all the examples published below not only by creating and running a BAT file containing these commands, but by copying them directly to the command line.
To open the command line in the right place (in the folder with files, for example), you need to call the context menu (RMB) with the Shift key held down:
command line call
You can read about how to work with the command line in this article. We pass directly to the teams. Continue reading



