How does antivirus work
 Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
The lion’s share of such programs is aimed at Windows. Firstly, this operating system is the most common in the world. Secondly, it is vulnerable to attacks and hacking attempts due to its popularity. Thirdly, the audience using the OS does not shine with special knowledge of computer literacy. There is also spyware for Linux and MacOS, but it is completely useless from the word.
How antiviruses work
If you look, then any product, whether it be Kaspersky, Avast, Nod 32 and not only, works on the same principle as the virus:
monitors traffic;
scans ports
Deletes and modifies files;
rules the registry;
heavily loads the system with “left” services;
collects statistics and sends it to the developer.
But the system at the same time works quite stably and quickly. Another thing is that putting two antiviruses in parallel, if possible, is pretty stupid. The machine will start to slow down hellishly, the files of the two programs will perceive each other as something suspicious, trying to “gobble up” one of the one, the rest of the software will download the missing pieces from the network and the process will be repeated again. It will end with the fall of the OS.
How antivirus protects the owner
If you don’t go into the details of the software that many may find obscure, I’d like to highlight 3 main principles of antivirus actions in relation to spyware:
diagnostics;
prophylaxis;
treatment.
In the first case, the software checks all the places on the HDD, RAM and removable media. Priority is given to those areas that are most often hit by trojans (boot sectors, executable libraries, drivers, etc.). If the antivirus finds something, it automatically notifies the user.
Treatment can be of two types:
attempt to cure file;
quarantine;
removal.
In the first case, the software will try in every possible way to restore the functionality of one or more files. If all else fails, infected objects will be permanently deleted from the PC. The integrity of the system may suffer and it will have to be restored.
Files are quarantined if they are valuable to you or contain important data. In the future, you can try to cure the object yourself, or with the help of a specialist.
Prevention – systematic scanning by antivirus in the background. You can not suspect about its work (if the PC is powerful and there are enough resources). In this mode, the antivirus scans all opened programs, folders, files, and more. If he finds a virus or something suspicious, he will immediately inform the owner.
Detection methods
To date, there are 3 key ways to search for various worms and all other obscurantism that spoils the OS:
signature method;
heuristic method;
firewall (firewall).
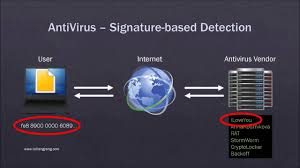
Signatures
The principle of the signatures is as follows: the anti-virus laboratory detects a new virus and then analyzes it, identifying the signature – a special digital sign of a pest (like a fingerprint). Signatures are added to the database, which the user downloads when updating.
The advantages are that the method is reliable and has been used for a very long time. Also relatively fast.
Of the shortcomings, I want to note a huge number of such trojans that have similar signatures. Because of this, you have to develop a template that is entered from the database, and then unwanted software is searched for on its basis. In this case, false positives of antiviruses sometimes occur, which periodically annoys.
Heuristic
Many programs have a built-in heuristic module for virus scanning. The bottom line is to check all the programs and files that you run on your PC. If the antivirus detects something dubious or suspicious, it will immediately display a message.
Advantages in the prospects of the direction of such a method and the ability to respond to those threats that are not in the signature database.
The disadvantage is “dampness,” because false positives for safe software are common. There are frequent cases of disabling the heuristic module, which is “annoying”, because of which the system puts a potential threat. And this method is quite voracious to PC resources.
Firewall
Firewalls protect the network, i.e. local and global connections. This module is often independent and is sold as a separate program, or is already integrated into the system (the Windows firewall is an example of this). The software controls incoming and outgoing traffic, limiting the ability to connect to certain resources (white and black lists).
Among the advantages, we note the opportunity to create a “free” Internet, working exclusively with a list of trusted sites. You can also install it on one of the local gateways, creating school or institute networks of a narrow focus (without social networks, instant messengers and other “black” sites).




