spam – otherwise
Causes and methods for resolving error 0x0000007b
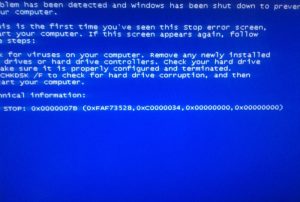 If a problem 0x0000007b occurs, a blue screen appears on the monitor. The PC stops responding to any action. In some cases, a reboot may help. Such a problem often occurs during reinstallation of Windows XP, 7, 10 appears when working with applications and games.
If a problem 0x0000007b occurs, a blue screen appears on the monitor. The PC stops responding to any action. In some cases, a reboot may help. Such a problem often occurs during reinstallation of Windows XP, 7, 10 appears when working with applications and games.
Error
The information code is located at the bottom of the screen and reports that there is no access to the system directory at boot time. There are a large number of reasons for the appearance of such an error, therefore, to solve the problem, you need to take appropriate measures.
When does this error occur? Continue reading
Why Kaspersky is not installed
 The question of why Kaspersky is not installed is asked by many users. It is no secret to anyone that Kaspersky Anti-Virus is today considered one of the most popular anti-virus programs. So why is there a problem with installing this software, why do errors appear that force the user to choose some other anti-virus program? Let’s talk about this in more detail.
The question of why Kaspersky is not installed is asked by many users. It is no secret to anyone that Kaspersky Anti-Virus is today considered one of the most popular anti-virus programs. So why is there a problem with installing this software, why do errors appear that force the user to choose some other anti-virus program? Let’s talk about this in more detail.
Previous version of Kaspersky deleted incorrectly
If Kaspersky is not installed, the reasons for this may be different. For example, you did not uninstall the previous version of the program. This error is the most common. Some users either incorrectly remove Continue reading
How to hack a computer
 A home computer is an excellent and at the same time the most vulnerable place to attack. Hacking someone else’s PC, you can not only view the information stored in his memory, but also find out the numbers of bank and virtual cards, and then withdraw all money from them. The resources of the computer itself – the space of the hard disk, the speed of the processor, as well as the speed of the Internet connection will help in attacking other computers that are on the same network as the potential victim. Before you commit a hacker attack, think that the case is illegal and criminally punishable. If this does not scare you, our article is for you.
A home computer is an excellent and at the same time the most vulnerable place to attack. Hacking someone else’s PC, you can not only view the information stored in his memory, but also find out the numbers of bank and virtual cards, and then withdraw all money from them. The resources of the computer itself – the space of the hard disk, the speed of the processor, as well as the speed of the Internet connection will help in attacking other computers that are on the same network as the potential victim. Before you commit a hacker attack, think that the case is illegal and criminally punishable. If this does not scare you, our article is for you.
Hacking a computer through Dark Comet
Dark Comet, or “Rat,” is one of the most popular means of remote computer control. Although the official Continue reading