monitoring mode
Why Kaspersky is not installed
 The question of why Kaspersky is not installed is asked by many users. It is no secret to anyone that Kaspersky Anti-Virus is today considered one of the most popular anti-virus programs. So why is there a problem with installing this software, why do errors appear that force the user to choose some other anti-virus program? Let’s talk about this in more detail.
The question of why Kaspersky is not installed is asked by many users. It is no secret to anyone that Kaspersky Anti-Virus is today considered one of the most popular anti-virus programs. So why is there a problem with installing this software, why do errors appear that force the user to choose some other anti-virus program? Let’s talk about this in more detail.
Previous version of Kaspersky deleted incorrectly
If Kaspersky is not installed, the reasons for this may be different. For example, you did not uninstall the previous version of the program. This error is the most common. Some users either incorrectly remove Continue reading
How to hack a computer
 A home computer is an excellent and at the same time the most vulnerable place to attack. Hacking someone else’s PC, you can not only view the information stored in his memory, but also find out the numbers of bank and virtual cards, and then withdraw all money from them. The resources of the computer itself – the space of the hard disk, the speed of the processor, as well as the speed of the Internet connection will help in attacking other computers that are on the same network as the potential victim. Before you commit a hacker attack, think that the case is illegal and criminally punishable. If this does not scare you, our article is for you.
A home computer is an excellent and at the same time the most vulnerable place to attack. Hacking someone else’s PC, you can not only view the information stored in his memory, but also find out the numbers of bank and virtual cards, and then withdraw all money from them. The resources of the computer itself – the space of the hard disk, the speed of the processor, as well as the speed of the Internet connection will help in attacking other computers that are on the same network as the potential victim. Before you commit a hacker attack, think that the case is illegal and criminally punishable. If this does not scare you, our article is for you.
Hacking a computer through Dark Comet
Dark Comet, or “Rat,” is one of the most popular means of remote computer control. Although the official Continue reading
How does antivirus work
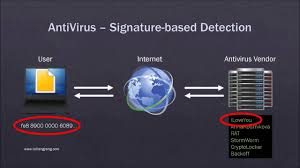 Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
The lion’s share of such programs is aimed at Windows. Firstly, this operating system is the most common in the world. Secondly, it is vulnerable to attacks and hacking attempts due to its popularity. Thirdly, the audience using the OS does not shine with special knowledge of computer literacy. There is also spyware for Linux and MacOS, but it is completely useless from the word. Continue reading