how antivirus
How does antivirus work
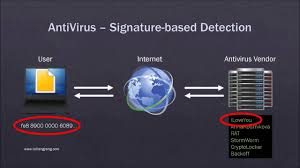 Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
Few people think about how antivirus software works. Often it is installed, periodically updated, but this is where the care for the program ends. The antivirus itself is a means of combating viruses, trojans, spyware, worms, backdoors and other garbage, which we scoop in large quantities from the Internet.
The lion’s share of such programs is aimed at Windows. Firstly, this operating system is the most common in the world. Secondly, it is vulnerable to attacks and hacking attempts due to its popularity. Thirdly, the audience using the OS does not shine with special knowledge of computer literacy. There is also spyware for Linux and MacOS, but it is completely useless from the word. Continue reading



