Apple’s latest
How to install WordPress on hosting
 In order to install WordPress on hosting, you need to follow a few steps that we will do now. So, how to install WordPress on hosting.
In order to install WordPress on hosting, you need to follow a few steps that we will do now. So, how to install WordPress on hosting.
Step # 1 – Creating Your Domain Directory
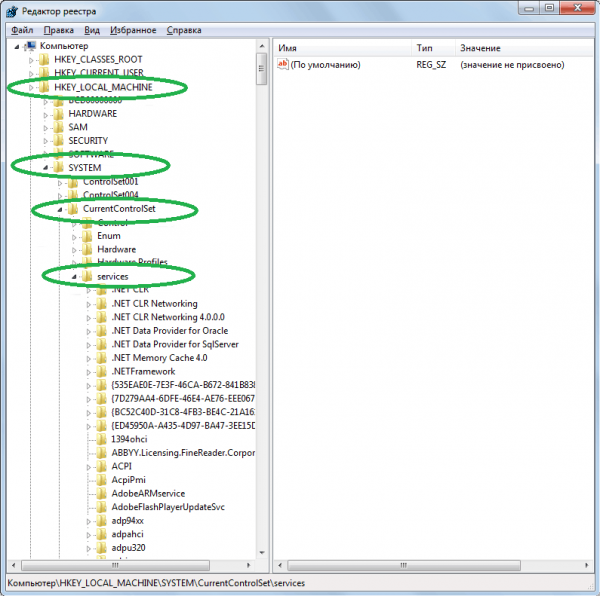
Log in to the control panel of your hosting (example on the IspManager 5 panel), create a domain that you should have already registered. If you have not registered a domain, it is best to do it here.
To create the root folder of a domain, click on the menu on the left “www” – “www-domains”. Then to “create”. After that, a window with the WWW-domain tab will open in front of you. Enter the following: Continue reading
Advanced CSS Hacks Collection
 A hack is a method that allows CSS to be perceived only by a specific browser.
A hack is a method that allows CSS to be perceived only by a specific browser.
Hacks can be used not only to fix bugs in the layout, but also if certain browser features are used to speed up the rendering of a web page in it (for example, CSS3 properties)
ALL KNOWN CONDITIONAL COMMENTS IN IE
Despite their fame, there are many rarely used ones.
For example, a stylesheet that will be visible to all browsers except IE versions 5-8.
<! – [if! IE] -> <link href = “styles.css” rel = “stylesheet” media = “all” /> <! – [endif] -> Continue reading
CSS layouts: fixed, rubber, elastic. Pros and cons
 What layout layout (using Cascading Style Sheets, CSS) can be considered the best? Each of them has its own hacks (quirks) and its own unique pros and cons. Will one of them be more user friendly than everyone else? How easy will it be? What problems do each of them have and how to get around them? Is one of them easier to compose than the rest? Is there any defective, completely unsuitable among them? Most likely, many will unequivocally answer these questions, but I will not be in such a hurry. I like each of these layouts, and each is applicable in one way or another, if you do it wisely and carefully check the ease of use and equal accessibility for all categories of users. All of them are part of the presentational layer for the website, so most accessibility issues arise from the correct use of semantics and general layout rules. Next, I Continue reading
What layout layout (using Cascading Style Sheets, CSS) can be considered the best? Each of them has its own hacks (quirks) and its own unique pros and cons. Will one of them be more user friendly than everyone else? How easy will it be? What problems do each of them have and how to get around them? Is one of them easier to compose than the rest? Is there any defective, completely unsuitable among them? Most likely, many will unequivocally answer these questions, but I will not be in such a hurry. I like each of these layouts, and each is applicable in one way or another, if you do it wisely and carefully check the ease of use and equal accessibility for all categories of users. All of them are part of the presentational layer for the website, so most accessibility issues arise from the correct use of semantics and general layout rules. Next, I Continue reading