Why everyone hated Apple and why they were wrong
 Apple’s latest technical solutions have made a lot of noise. In the iPhone 7, the jack slot disappeared, in the new MacBook the usual connectors are replaced with USB Type-C and there is no memory card slot. Poster Daily recalls all the joys that engineers from Cupertino deprived us of, and why it is difficult to argue with them.
Apple’s latest technical solutions have made a lot of noise. In the iPhone 7, the jack slot disappeared, in the new MacBook the usual connectors are replaced with USB Type-C and there is no memory card slot. Poster Daily recalls all the joys that engineers from Cupertino deprived us of, and why it is difficult to argue with them.
Apple for 30 years with an enviable persistence has been producing computers of closed architecture under the control of its own operating system. Neither the popularity of the PC as a gaming platform, nor the recognition in 2006 that Intel chips were better than their own could convince them of this. It turns out that the company, which we used to consider the most important developer of innovations, is in fact very conservative and rational in the market. By tradition, Apple itself decides what is needed and what Continue reading
Apple Pay: what is it and how to use it
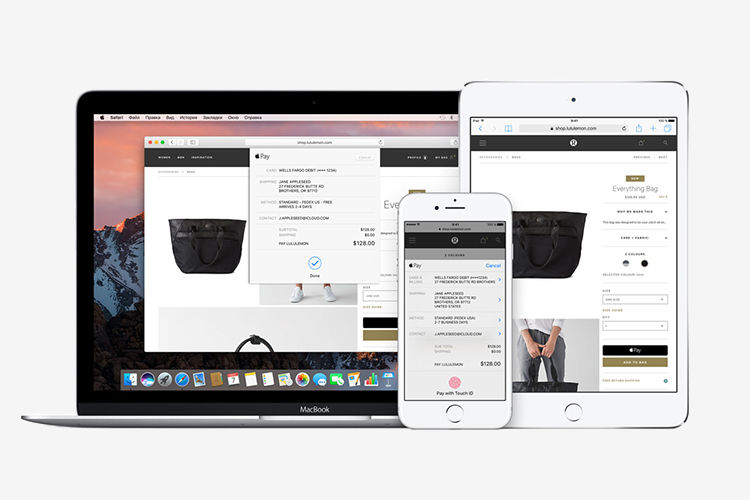
 Apple Pay is a payment system that allows you to pay for goods in stores by attaching an Apple mobile device to the terminal. The system works according to the NFC protocol and only on terminals that accept contactless payments (they must have a PayPass or PayWave label). The system is compatible only with models older than the iPhone 6, including the iPhone SE, as well as with the Apple Watch. In the latter case, the system will be able to configure through the iPhone 5, 5s and 5c.
Apple Pay is a payment system that allows you to pay for goods in stores by attaching an Apple mobile device to the terminal. The system works according to the NFC protocol and only on terminals that accept contactless payments (they must have a PayPass or PayWave label). The system is compatible only with models older than the iPhone 6, including the iPhone SE, as well as with the Apple Watch. In the latter case, the system will be able to configure through the iPhone 5, 5s and 5c.
To pay, you need to bring the gadget to the terminal, select the card in the application and attach your finger to the Touch ID sensor. On Apple Watch, a payment is launched by double-clicking on the power button and does not require special authorization. Neither Apple Pay nor other payment services charge Continue reading
How hackers turn our printers, cameras and thermostats into sinister cyber army
 In the fall, several large hacker attacks took place in which IoT devices were used. One of them is for Russian banks. The Daily Poster tells the story of other interesting hacks and explains how attackers harm people through light bulbs and refrigerators.
In the fall, several large hacker attacks took place in which IoT devices were used. One of them is for Russian banks. The Daily Poster tells the story of other interesting hacks and explains how attackers harm people through light bulbs and refrigerators.
Internet of things attacks Russian banks
On Thursday, November 10, five large Russian banks were subjected to DDoS attacks – a large number of junk requests came to sites that loaded servers and made sites inaccessible. The attacks went to the Moscow Exchange, Alfa Bank, Sberbank, Otkritie Bank, VTB Bank and Rosbank. Almost all banks managed to cope with the load. Among the possible organizers of the attack was a hacker under the nickname vimproducts, whose customers were allegedly dissatisfied with Russia’s interference in the Continue reading
5 fashionable ways to hide from face identification
 Today, the face recognition algorithm is used everywhere. And not only in professional tracking systems or smart web services, but in various entertainment applications and basic functions like autofocus. Poster Daily decided to try to trick the algorithm with makeup.
Today, the face recognition algorithm is used everywhere. And not only in professional tracking systems or smart web services, but in various entertainment applications and basic functions like autofocus. Poster Daily decided to try to trick the algorithm with makeup.
Different systems for recognizing a human face have different goals, which is why their algorithms differ. One of the first systems that were able to establish a person’s identity from a photo looked for nodal points on the image that made up the main features of the face, and measured the distance between them. The main measurement parameters are the distance between the eyes, the width of the nose, the depth of the orbit, the shape of the cheekbones, and the length of the jaw line. Key figures in digital terms Continue reading
Windows operating systems
 In this article we will look at the types of Windows NT operating systems. Windows NT is not Windows2000 or any other. This is a series, or rather the platform, on the basis of which the OS is being developed. Almost the entire Windows family is based on this platform. In addition to NT, there is also a 9x platform, which includes Windows95, Windows98, and WindowsME.
In this article we will look at the types of Windows NT operating systems. Windows NT is not Windows2000 or any other. This is a series, or rather the platform, on the basis of which the OS is being developed. Almost the entire Windows family is based on this platform. In addition to NT, there is also a 9x platform, which includes Windows95, Windows98, and WindowsME.
Due to the fact that there were concerns about the malfunctioning of programs written taking into account old versions of the OS, the 10th version of the operating system was released immediately after the eighth. Otherwise, the 9th version in the version could be interpreted by the program as the operating system of the 9th series. Details about what NT is in this article. Continue reading